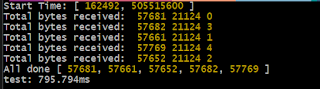
AKS - couldn't get current server API group list dail tcp lookup 443 timeout
Well this sounds like you have an issue connecting (obviously) - Goto Azure portal -> Find your AKS cluster and click on the connect button. Then you need to provide az aks get-credentials --resource-group my-resource-group --name myaks-cluster Well sometimes we do forgets to re-authenticate to a new cluster. You can use the following to test connectivity to your cluster - assuming you have access to the kubernetes API az aks command invoke \ --resource-group my-resource-group \ --name myaks-cluster \ --command "kubectl get pods -n kube-system"